Sensitive Data Protection
Sensitive data management is meant to avoid the dissemination of the senstive information accross the EMV Level 2 code. In switstack moka's architecture, this is the role of the Reader service in collaboration with the HSM (which stores certificates and revocated certificates).
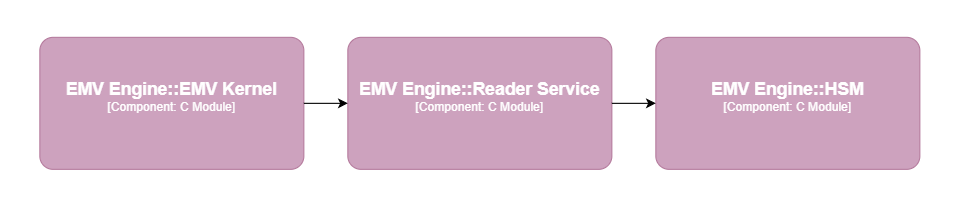
Note
For a better readability, the model above doesn't represent the message broker but all services communicate through it.
Reader
Data model
The list of protected data is made of the following tags:
typedef struct moka_sred_data {
/** track 2 equivalent data */
uint16_t _57_length;
uint8_t _57[19];
/* application pan */
uint16_t _5A_length;
uint8_t _5A[20];
/* df name */
uint16_t _84_length;
uint8_t _84[16];
/* ca public key index */
uint16_t _8F_length;
uint8_t _8F[1];
/** issuer public certificate */
uint16_t _90_length;
uint8_t _90[READER_SRED_MAX_KEY_LENGTH];
/** issuer public remainder */
uint16_t _92_length;
uint8_t _92[READER_SRED_MAX_KEY_LENGTH];
/** transaction date */
uint16_t _9A_length;
uint8_t _9A[3];
/** issuer public key exponent*/
uint16_t _9F32_length;
uint8_t _9F32[3];
/** icc public key certificate */
uint16_t _9F46_length;
uint8_t _9F46[READER_SRED_MAX_KEY_LENGTH];
/** icc public key exponent*/
uint16_t _9F47_length;
uint8_t _9F47[3];
/** icc public key remainder */
uint16_t _9F48_length;
uint8_t _9F48[READER_SRED_MAX_KEY_LENGTH];
} moka_sred_data_t;
These data are encapsulated by the Reader service because it also manages the coupling with cards. During APDU exchanges, they are captured, obfuscated, and stored locally to the Reader service for further EMV Level 2 processing. Additionally, the service Reader exposes the following functional services to address EMV steps based on sensitive data:
Functional services
| Reader Services | Description |
|---|---|
| READER_SERVICE_GET_ISSUER_KEY | Get issuer key for SDA processing |
| READER_SERVICE_GET_ICC_KEY | Get icc key for CDA processing |
| READER_SERVICE_SET_SIGNED_RECORD | Flag a record participating to offline data authentication |
| READER_SERVICE_GET_CAPK_INDEX_PRESENCE_STATUS | Indicate whether a capk ined is present in certificate database |
| READER_SERVICE_STORE_RRP_IN_TRACK_2 | Store discretionary data into track 2 equivalent data |
| READER_SERVICE_COMPARE_PAN | Compare pan values from tag 57 and pan from tag 5A |
| READER_SERVICE_COMPUTE_SSD_SHA | Perform SHA computing required to verify SDA certificate, tag 93 |
That way, all these information are never used outside the logic of the Reader service. This architecture principle limits the magnitude of the PCI zone, and - thanks to the message broker - enables simple realization of physical architectures that can leverage on a secure element, for example.